Title: ANOMALY DETECTION FOR SMART PHONES USING CLOUD-BASED INTRUSION DETECTION AND RESPONSE SYSTEM
Authors: Sahil Sakhala, 3rd Year, BE, Computer Engineering
Kshitij Khakurdikar, 4th Year, BE, Computer Engineering
College: K.K. Wagh Institute of Engineering Education & Research Hirabai Haridas Vidyanagari, Nashik
ABSTRACT:
As smart mobile phones, which are also called as smartphones, are getting more complex and more potent to efficiently provide more functionalities. Concerns are augmenting regarding security threats against the smartphone users. Smartphones are phones with advanced capabilities like those of personal computers (PCs), are appearing in more people’s pockets, purses, and briefcases. As the smartphones are becoming widespread so do the security threats and vulnerabilities facing this technology. Since smartphones use the same software architecture as in PCs, they are vulnerable to be exposed to similar threats such as in PCs. Due to increase usage of security features; there is the big impact on the battery life of the smart phones. As if in case, a smartphone is attacked and some antivirus is working for protection then it will consume huge chunk of resources. There might be some harmful program which can make antivirus running for long time which in turn consumes system resources and battery. The smartphones have less storage and computational power to put into effect highly complex algorithms for intrusion detection and implementing signature based attack detection. Now with emergence of technology, cloud computing concept also comes into emergence and this technology is growing at very fast rate to fulfil the huge requirement. In this paper, we propose a cloud based intrusion detection and response system for detection of anomaly in smartphones that will provide continuous in-depth forensic analysis to detect any misbehaviour in network.
KEYWORDS— Smartphone, intrusion detection, cloud environment, forensic analysis.
INTRODUCTION:
Over the last decade, the popularity of handheld devices such as smartphones has increased tremendously Smartphones, as extremely fast-growing type of communication devices, offer more advanced computing and connectivity functionalities than contemporary mobile phones by conceptually integrating handheld computers capabilities with phone devices. Smartphones are becoming a more integrated and prevalent part of people’s daily lives due to their highly powerful computational capabilities, such as bill paying, online banking and email applications. Being an “all-in-one” device, smartphones are increasingly getting attractive to a wide range of users .Following smartphones increasing popularity, attackers have also been interested in attacking to such platforms.
NEED FOR CYBER SECURITY OF SMARTPHONES:
In fact, a large number of smartphone malware have attempted to exploit unique vulnerabilities of smartphones. The new generation of smartphone malware attacks has increased in sophistication and is designed to cause severe financial losses (caused by identity theft) and disruption of critical software applications. As a case in point, the smartphone virus Cabir spreads and populates through the Bluetooth interface of smartphone. Another recent smartphone security study shows that Trojans can steal sensitive information using some voice recognizing algorithm that is talked through smartphones. In December, 2004, a Trojan horse was disguised in a video game which signalled the risks associated with smartphones that could potentially compromise the integrity and confidentiality of personal information contained in smartphones. Apart from invading privacy and security of the smartphone users such threats also manage to form botnets by which communication infrastructures can face large-scale co-ordinated attacks.
Malware such as Geimini and DroidDream will attempt to get root privilege, leak personal information and abuse functions of the smartphone. Dikinson states that the antivirus companies take time to update their signature repositories, and when the new kind of malware is created and placed onto the network, hackers have substantial amount of time to perform their attacks before malware signatures are updated across different machines.
As their data transmission become affordable and available, usage of smart mobile phones for online financial transactions, social networking, mobile learning and web browsing become which may also cause several security issues. User can get malware on their smartphone just as it can bypass security and get on PC. Most viruses are picked up from downloading a corrupt email attachment or by some activities on social-networking sites or visiting a phishing website. You can also get viruses on your phone through shared links on mobile social networking apps and other peer-to-peer sharing applications. As architecture of such devices are much similar to classic personal computers in terms of functionality as well as performance, common security threats like worms, Trojans and viruses are also affecting smart phones. To protect smartphones in the same way as desktop-PC same security algorithms are required to be used. But these algorithms are highly resource consuming and can be complex too, so they cannot be executed on such smart mobile phone as they are constrained by power, computational and storage limitations.
SECURITY THREATS:
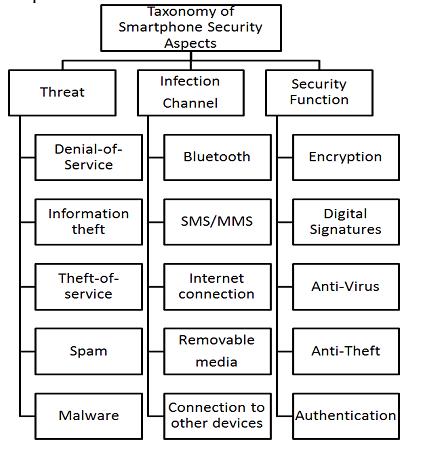
Figure1 presents the most frequent types of threats and infection channels, as well as corresponding security functions suitable to protect smartphones.
1) Threats:
Denial-of-Service attacks against smartphones are carried out by flooding with a large number of packets to the device to consume system resources or battery.
Information theft occurs when hackers attack smartphones to obtain personal information which might be sensitive or confidential.
Theft-of-service occurs when malware uses smartphone resources, for instance, to send expensive SMS messages.
Spam categorizes attacks where mobile users are targeted involuntarily with advertising, messaging, and other similar information.
Figure1. Taxonomy of frequent threats, infections channels and security functions
2) Infection Channels:
Bluetooth viruses may infect mobile devices. The most well-known virus of this kind is Cabir. The Short Message Service (SMS) or Multimedia messaging service (MMS) can be used by smartphone viruses to spread within networks.
3) Security Function:
Since the sensitive or valuable information is being increasingly stored in smartphones and/or transmitted over the network, this data should be encrypted to ensure that the confidentiality of the information is not compromised.
CURRENT SECURITY SOLUTIONS:
1) ANTI-VIRUS:
Almost everyone these days are aware about the various viruses, Trojans and spyware that attack PCs and to encounter them, they have anti-virus software that affords them some protection. Apart from anti-virus there are few other software that are used for security of smartphones which are available in market and thus enhance the security of smartphones.
2) INTRUSION DETECTION AND RESPONSE SYSTEM:
In designing an IDS, it was highlighted by [10], that response issues are amongst the important issues (i.e.; data collection, data pre-processing, intrusion recognition) to be considered. A first attempt to organize existing research works in the area of intrusion response systems was done by in 2007. Intrusion detection systems (IDSs) are software or hardware systems that automate the process of monitoring the events occurring in a computer system or network and analysing them for signs of intrusions.
IDS plays a role in incident handling processes by performing detection, analysis, producing alerts and also execution of counter measures. IDS also act as a security tools to identify illegitimate users, attacks and vulnerabilities that could compromise security of a resource and the proper functioning of computer systems.
In the existing the intrusion software that is downloaded consumes memory and power. It is not a proactive defence mechanism.
DISADVANTAGES OF PREVIOUS SYSTEM:
There are various newest growing threats that attack smartphones. Smartphones are like mini computers in themselves and can become infected with all types of malware. But antivirus is proving to be ineffective for smartphones as there are several limitations in practice. Depending upon the signature database of the antivirus software, some antivirus engines cannot detect sophisticated virus attacks. Hence, the detection coverage of single antivirus engine can be considerably low.
The past solutions for smartphone security encounter several limitations in practice. Many of such approaches are based on running a lightweight intrusion detection process on the smartphones; these schemes fail to provide effective protection as they are have limited storage, power and computational resources. Due to the increase of sophisticated attacks, several techniques for detecting malware on various platform have been introduced. An IDS by its nature is a passive security tool to watch and assess the traffic or network activity without impacting the traffic. In addition, most of such approaches are based on detecting malware/intrusions by looking for some specific signatures downloaded from a database. This, first of all, requires a large amount of storage on the device, and, secondly, such a signature-based approach is easily evaded by introducing zero-day threats.
Using firewalls, antivirus scanners, spyware scanners and rootkit detectors on smart mobile devices proves to be difficult, mainly because of lack of resources like battery longevity, computing power and storage. To overcome such limitations, Cloud Computing provides plenty of software, processing power and services over internet. Compared to mobile phones it reduces bandwidth usage, processing power and energy consumption. Cloud computing, and specifically Security as a Service, changes the dynamics of protecting smart phones over a network.
CLOUD COMPUTING:
Cloud computing portends a major change in how we store information and run applications. Cloud computing can be used by anyone without having any end-user knowledge which are storage, data access, security and software services.
Cloud computing has emerged as a new computing paradigm providing hosted services by exploiting the concept of dynamically scalable and shared resources accessible over the internet. Cloud is best delivery model for IT services based on internet protocols.
Cloud computing at its foundation is an broader concept of shared services and infrastructure convergence. This type of data centered environment allows any user to get their applications up and with easier manageability and running faster, less maintenance, and enables IT to more rapidly adjust IT resources to meet varying and unpredictable business demand.
PROPOSED SOLUTION:
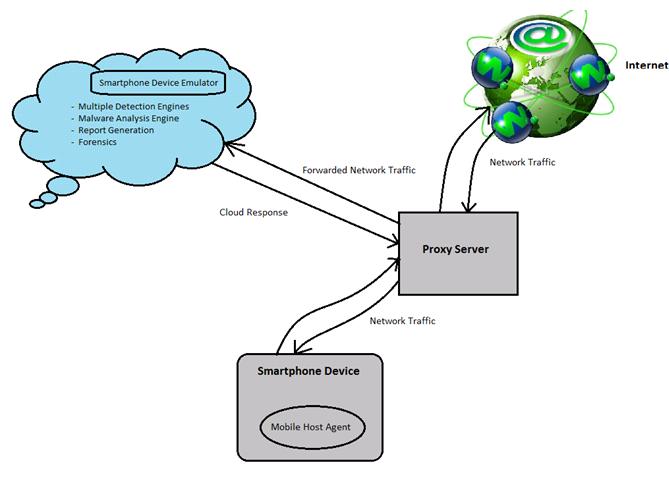
In the proposed system a proactive defense mechanism is being developed where the smartphone user is given the alert that the file is corrupt before it is downloaded. The system is developed in cloud so all the registered user can use the system at a single time. A lightweight process which is called as mobile host is installed in the form of application on registered device. It inspects all the file activity on the system. While the user will try to download any file from internet, the mobile host agent will divert all the traffic to cloud via proxy server and and run multiple detection engine in parallel by hosting them on emulated device. The use of virtualization to run multiple detection engines increases the coverage malware detection.
While diverting the traffic to the cloud, proxy server will also function for detection of an anomaly in network. It will detect any attack in network and notify user before attack can actually occur on smartphone and will thus prevent identity-theft attacks.
Malware Analysis Engine will scan all the files to detect any anomaly and create signatures of all files. If any malware of its first kind is detected, then it will update that signature to all the anti-virus so that they can detect that malware in future.
Most of the Trojans or few other kind of malware tries to connect to internet so that sensitive information can be transferred via internet. So in such cases, forensics will come into play. It will try to find the source which is spreading any such nuisance and automated report will be generated. It will update its network setting, which will block any such sources and alert user. Detection engine will also detect fraudulent emails.
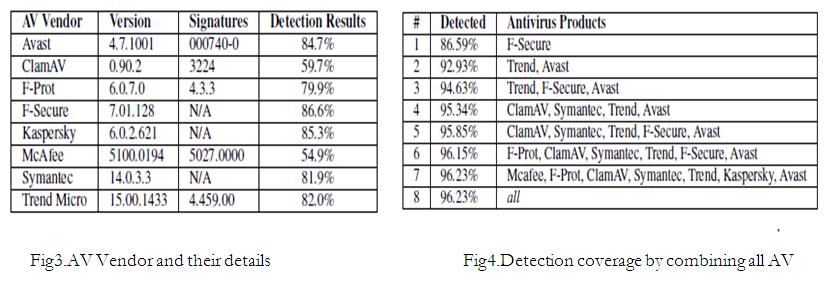
No single anti-virus vendor can provide a complete protection against any malware or any attack. Fig2 shows list of different AV Vendors, their version, signatures and detection results. This statistics clearly shows that no AV
Vendor can provide 100% result. But if all the AV Vendors are used simultaneously then they can comparatively provide much more assured security for smartphone. Its details can be seen from fig4 which shows percentage of detection by an AV individually and by all of them together, which is much higher than any individual AV product.
A smartphone should be registered by its owner to be protected by the framework to the framework’s online registration system. The client should register their smartphone on frameworks service to be protected by the mentioned framework so that an exact copy of their smartphone is made and registered on cloud. Additionally, the client is asked to install a very light-weight software agent on the smartphone that automatically would configure the proxy settings. A proxy server is responsible for duplicating the communication between the smartphone and the Internet and forwarding it to the smartphone emulation environment in cloud where the detection and forensics analysis is performed. It’s to be noted that this does not disrupt the usual communication between the smartphone and the Internet.
CONCLUSION:
This paper presented an ideal way to detect anomaly in smartphone using cloud along with intrusion detection service that provides optimal protection and in-depth forensic analysis. This research aims to enhance the current detection engine by incorporating intrusion response module and forensic module which will formulate response effectiveness using cost-sensitive approach and will also automate report generation for forensic analysis. The system identifies the intrusion in the specific smartphone using cloud. If any illegitimate activity is detected, the system will take the felicitous response actions to handle the threat. The mobile host agent clusters all user and sensor inputs to the device, it consigns them to the emulation environment, and it waits for emulation environment in order to take the required actions. Detection engine will also detect fraudulent emails based on past records of DNS. Hence it will prove to be an extremely efficient and economic method in terms of cost, security and utilization of system resources for anomaly detection in smartphone.
References:
- Amir Houmansadr, Saman A. Zonouz, and Robin Berthier, “A Cloud-based Intrusion Detection and Response System for Mobile Phones,” IEEE, 2011.
- Rohit S. Khune and J. Thangakumar “A Cloud-Based Intrusion Detection System for Android Smartphones” 012 International Conference on Radar, Communication and Computing (ICRCC).
- Muhamed Halilovic, “Intrusion Detection on Smartphones,” Official Appledocumentation:http://developer.apple.com/library/ios/#documentation
- Naqliyah BT Zainuddin, “A Study on Android-based IDS: A Propose for Cost-sensitive Based Intrusion Response System Advances in Remote Sensing, Finite Differences and Information Security.
- Namitha Jacob, “Intrusion Detection in Cloud for Smart Phones,” www.ijreat.org.
- Stojan Kitanov, Danco Davcev “Mobile Cloud Computing Environment as a Support for Mobile Learning”. In CLOUD COMPUTING: The Third International Conference on Cloud Computing, GRIDs, and Virtualization, 2012, pages 99-105.
- J. DICKINSON, The new anti-virus formula. Messaging News Press, 2005.
- J. Jamaluddin, N. Zotou, and P. Coulton. “Mobile phone vulnerabilities: a new generation of malware”. In Consumer Electronics, IEEE International Symposium, 2004, pages 199 – 202.
- IBM Corporation, “IBM X-Force 2011 Mid-year Trend and Risk Report”https://www14.software.ibm.com/webapp/iwm/web/signup.do?source=swg-spsm-tiv-sewp&SPKG=IBM X-Force-2011-Mid-year, 2011, [retrieved: May, 2012].
- S. Xiaonan and W. Wolfgang, “The Use of Computational Intelligence in Intrusion Detection SystemsP: A Review,” Soft Computing, no. November, 2008.
- N. Stakhanova, S. Basu, and W. Johnny, “A taxonomy of intrusion response systems,” Computer, vol. 1, no. 1, pp. 169-184, 2007.
- http://anti-virus-software-review.toptenreviews.com/mobile-phones-are-under-malware-attack.html/?cmpid=ttr-bnd